What is a PNPT?
Before jumping into my exam preparation and experience, let us quickly cover what a Practical Network Penetration Tester (PNPT) is. A PNPT is someone who successfully compromised the exam Domain Admin, established persistence, submitted a penetration test report, and gave a live debrief of the report. Exam takers are given 5 days to complete the penetration test objectives and 2 days to create the report.
PNPT Preparation
I began my PNPT exam preparation on October 3, 2022, and finished on October 17, 2022. During this time period all of my free-time and energy was spent on training.
I should mention that I passed the Offensive Security Certified Professional (OSCP) exam the month prior, which played a major role in my preparation. If you are interested in learning about my preparation for the OSCP exam click here. You can also checkout my official OSCP exam guide here.
The following materials were used during my preparation:
- TCM Security’s Practical Ethical Hacking course
- TCM Security’s Open-Source Intelligence (OSINT) Fundamentals course
- TCM Security’s External Pentest Playbook course
- TCM Security’s Windows Privilege Escalation for Beginners course
- TCM Security’s Linux Privilege Escalation for Beginners course
At the time of writing, all of the courses above are $29.99 each. You can purchase the Academy All-Access Membership for $29.99 a month, giving you access to all of the courses. If you purchase the courses individually, you have access to them for life. I opted for the Academy All-Access Membership, meaning I no longer have access to the courses if I cancel my membership.
Course Recommendations
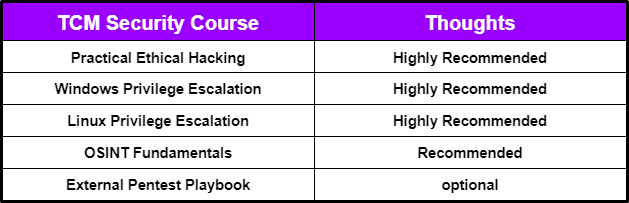
Breakdown of TCM Security Courses
Practical Ethical Hacking
The practical ethical hacking course overview on TCM Security’s website claims that no prior hacking knowledge is required, I agree! However, it is expected that the students have basic IT knowledge. The course does go over some basics but only to serve as a quick refresher.
This 25 hour long course covers the following:
- A Day in the Life of an Ethical Hacker
- Effective Notekeeping
- Networking Refresher
- Introductory Linux
- Introductory Python
- Hacking Methodology
- Reconnaissance and Information Gathering
- Scanning and Enumeration
- Exploitation Basics
- Mid-Course Capstone
- Exploit Development
- Active Directory
- Post Exploitation
- Web Application Penetration Testing
- Legal Documentation and Report Writing
- Career Advice
Quite honestly, you should look into taking this course whether you are preparing for the PNPT exam or not. My favorite aspect of the course is attacking your own AD lab using the techniques taught to you. Do not worry, the instructor guides you on building your AD lab environment. Building and attacking your own AD lab is not only fun, it is crucial to understanding the attacks and how they work.
Windows Privilege Escalation for Beginners
The guys over at TCM Security prefer for you to have some hacking and virtualization knowledge when starting the Windows Privilege Escalation for Beginners course. The course does a wonderful job demonstrating different Windows privilege escalation techniques.
Here is some of what is covered in this 7 hour course:
- Windows manual enumeration
- Windows automatic enumeration
- Kernel Exploits
- Password Hunting
- Registry Attacks
- Executable Files
- Schedule Tasks
- Startup Applications
- DLL Hijacking
- Service Permissions
- Windows Subsystem for Linux
- CVE-2019–1388
The downside is you need access to Hack The Box or TryHackMe for some of the course work. The instructor does go over all of the assignments, so you can watch him complete the tasks if you do not have access to Hack The Box or TryHackMe.
Linux Privilege Escalation for Beginners
Just like the Windows Privilege Escalation for Beginners course, TCM Security would like students to possess some hacking and virtualization knowledge prior to starting the Linux Privilege Escalation for Beginners course. In this course you will find various Linux privilege escalation techniques.
This 6.5 hour course covers the following:
- Linux manual enumeration
- Linux automatic enumeration
- Kernel Exploits
- Password Hunting
- File Permissions
- Sudo Attacks
- Shell Escaping
- Intended Functionality
- LD_PRELOAD
- CVE-2019–14287
- CVE-2019–18634
- SUID Attacks
- Shared Object Injection
- Binary Symlinks
- Environment Variables
- Capabilities Attacks
- Scheduled Tasks
- NFS
- Docker
Students get access to a custom lab with no installation required.
OSINT Fundamentals
This course focuses on OSINT tactics and techniques to help improve your investigative game. Prior Linux experience is preferred but not required.
This 9 hour course offers the following:
- OSINT Overview
- Effective Notekeeping
- Creating Sock Puppet Accounts
- Basic and Advanced Search Engine OSINT
- Image OSINT
- Email Address OSINT
- Breached Data OSINT
- People OSINT
- Phone Number OSINT
- Username OSINT
- Website OSINT
- Social Media OSINT
- Wireless Network OSINT
- OSINT with Tools
- Automating OSINT
- Report Writing
Overall, this course was extremely informative and useful for conducting research on companies and people. Remember, with great power comes great responsibility!
External Pentest Playbook
The External Pentest Playbook course is the one I least recommend of the courses I used to prepare. I still do believe you will find value out of it if you want to become a penetration tester.
The short 3.5 hour course covers the following:
- Objectives of an External Pentest
- Important Documents and Procedures
- Scope Verification and Client Communication
- Attack Strategies
- Vulnerability Scanning
- Common OSINT and Information Gathering Techniques
- Attacking O365/OWA
- Attacking Login Portals
- Bypassing MFA and Escalating Access
- Report Writing
- Identifying Common Pentest Findings
- Client Debriefs, Retests, and Attestations
This course was not needed for me to pass the PNPT exam. If you get the monthly subscription I recommend you skim through it, but if not, you are covered with the Practical Ethical Hacker course.
PNPT Exam Structure
The exam is essentially split into three components, compromising the Domain Controller, writing a professionally written report, and performing a live report debrief in front of TCM Security assessors. One needs to pass all three components in order to earn the PNPT certification.
Here is what you can expect to do during your PNPT exam experience:
- Perform OSINT to gather information on how to attack the target
- Use your AD attack exploitation skills to compromise the Domain Controller
- Create a professional report
- Give a live report debriefing
The PNPT Exam
I scheduled my PNPT exam attempt for October 18, 2022. This means I had until October 23, 2022, to compromise the Domain Controller. Things got real ugly real fast as I did not make any progress whatsoever on the first day. Since I had four days of exam time left, I did not panic.
On the second day, after carefully reviewing things, I finally made it into the internal network. I thought from this point onward things would be smooth sailing, boy was I wrong. On the third and fourth day I was throwing everything including the kitchen sink at the exam environment and got nothing. It was at the end of the fourth day when I thought I was probably going to fail the exam.
I approached the last day with as much enthusiasm as the first. If I was going to fail my first attempt, I made sure it would be because I was not good enough and not because I gave up. I kept searching and digging for new information and finally something happened. I had a buzzer beater moment when I came across a tool I was unfamiliar with and used it to break my way into another system.
On the last day, I compromised the Domain Controller and established persistence. The euphoria of successfully completing the penetration testing portion of the exam fueled me to crush the exam report.
PNPT Exam Report
Like the goofball that I am, I did not create a skeleton of the exam report prior to starting the exam. This is the same mistake I did when taking the OSCP exam. Luckily, TCM Security provided me with a penetration test report example.
I had a grueling time putting the exam report together as I was exhausted from the penetration test and sleep deprived. I used up the entire two days allotted to complete the report. I used Greenshot, a photo editor, to make my screenshots nice and pretty.
I ended up submitting a 38 page long report to TCM Security. They promptly responded to my submission and we scheduled a report debrief for the following day.

PNPT Exam Report Debrief
Once TCM Security review my exam report and informed me that I was eligible for a report debrief, I scheduled one for the very next day. The debrief is used for you to walk a member of TCM Security through your penetration test. Specifically, you are expected to highlight findings and remediation steps for said findings. I chose to share my screen and walk-through my report. You can also create a slideshow to share your findings this way.
The debrief was scheduled to be for no longer than 15 minutes but I ended up speaking with a member of TCM Security for roughly 45 minutes. This was not because I was being grilled on my findings or anything like that. I was just asking a lot of questions about some of the methods I used during the exam. I am extremely thankful for that TCM Security member as he was not required to do this.
PNPT Exam Final Thoughts
The experience I had taking the PNPT exam is the best exam experience I have had yet, it is not even close. I felt like I was on a real engagement and even had to remind myself a few times not treat the environment like a CTF.
I thought that the PNPT exam was going to be a walk-in-the-park after just passing the OSCP exam. The PNPT exam is no joke and it is right up there with the OSCP exam. My lack of respect for PNPT exam almost cost me to fail.
To address the elephant in the room, the PNPT certification is not as recognized as other penetration testing certifications. I believe this will not be the case for very long as it is only a matter of time before those in the field start to recognize the PNPT certification for what it is, a legitimate and practical penetration testing certification. I have been starting to see the PNPT certification beginning to be picked up by recruiters and even seen it in job postings.
Here are a few thoughts on what the PNPT certification represents:
- The ability to conduct reconnaissance on a target
- The ability to assess real-world networks
- The ability to stick to the rules of engagement
- The ability to be creative and think on your feet
- The ability to create and present actionable deliverables
- The ability to think critically and find solutions when none are apparent
The journey to becoming a PNPT was an incredible one and I recommend it to those interested in red teaming or penetration testing. I even recommend it to those like me who just want to do it for the knowledge, experience, and fun. Remember, when you cheat, you are only cheating yourself.
Thank you for stopping by! Be sure to follow my blog to get updates when I release new content that can help you improve your cybersecurity game.
Until next time…
— N3NU
Disclaimer: My content is for informational and educational purposes only. You may try out these hacks on your own computer at your own risk.

